2021. 5. 22. 18:08ㆍ카테고리 없음
- Mac App To Monitor Network Traffic
- What Is Network Traffic
- Mac App Network Traffic Ais
- Mac App Network Traffic Cameras
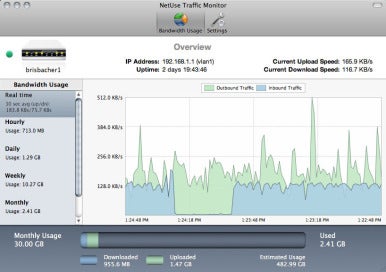
FlexiHub is among the most efficient Mac apps for developers who are building software solutions for iOS devices. The utility helps share iPhones and iPads over the network making them available for access from any remote machine, which means a developer can connect to an iOS device without having it physically attached to their Mac. IStumbler for Mac – WiFi analyzer app for Mac will display networks according to their types, i.e. Bluetooth, Bonjour or AirPort. WiFi Explorer – Detect issues that may be affecting connection and the performance of your network, such as channel conflicts, overlapping and configuration issues, etc. In the Activity Monitor app on your Mac, click Network (or use the Touch Bar) to see the following in the bottom of the window: Packets in, Packets out: The total number of packets received and sent. Packets in/sec, Packets out/sec: The speed of information being transferred (in packets per second). Data received, Data sent: The total amount of information moved (in megabytes).
Monitoring traffic on your network is important if you want to keep it secure and running efficiently. The information obtained by network traffic monitoring tools can be used in multiple security and IT operational use cases to identify security vulnerabilities, troubleshoot network issues and analyze the impact new applications will have on the network. These 5 tips should help you get the most out of your network traffic monitoring application.
1. Choose the right data source
Whatever your motive for monitoring network traffic, you have two main data sources to choose from:

- Flow data: which can be acquired from layer 3 devices like routers
- Packet data: which can be sourced from SPAN, mirror ports or via TAPs
Flow data is great if you are looking for traffic volumes and mapping the journey of a network packet from its origin to its destination. This level of information can help detect unauthorized WAN traffic and utilize network resources and performance. However, flow-based tools for monitoring network traffic lack the detailed data to detect many network security issues or perform true root cause analysis.
Packet data extracted from network packets can help network managers understand how users are implementing/operating applications, track usage on WAN links, and monitor for suspicious malware or other security incidents. Deep packet inspection tools provide 100% visibility over the network by transforming the raw metadata into a readable format and enabling network managers to drill down to the minutest detail.
2. Pick the correct points on the network to monitor
Naturally with agent-based software, you have to install software on each device you want to monitor. This is not only an expensive way of monitoring network traffic but it creates a significant implementation and maintenance overhead for IT teams. Furthermore, if your objective is to monitor activity on a BYOD or publicly-accessible network, agent-based software will not give you the full picture of user activity because it is impractical (and in some states illegal) to monitor activity on users´ personal devices.
Even with agent-free software, a common mistake many people make when deploying tools to monitor network traffic is that they include too many data sources at the start. There is no need to monitor every network point. Instead you need to pick points where data converges. Examples of this would be Internet gateways, Ethernet ports on WAN routers or VLANs associated with critical servers.
If you are new to getting tools in place to monitor network traffic, I would suggest you start by monitoring your Internet gateway(s). This can be an excellent source of security and operational data. This short video below explains how you can do this with Cisco switches – a similar approach can be applied to other switch vendors.
The image below shows a good approach when it comes to network traffic monitoring for most networks. A SPAN or mirror port is configured at the network core which allows for the capture of any traffic passing through. In my example this would allow me to capture traffic going to and from the Internet as well as traffic associated with important servers.
3. Sometimes real-time data is not enough
The ability to monitor network traffic in real-time is sufficient to achieve many objectives of network traffic monitoring, but sometimes real-time data is not enough. Historical traffic metadata is ideal for network forensics and is just as important if you want to analyze past events, identify trends or compare current network activity with the previous week. For these objectives, it is best to use tools for monitoring network traffic with deep packet inspection.
Some tools for monitoring network traffic choose to age data. This means the further back you go historically, the less detail you get. While this can save on disk space, it is not an ideal solution if you are trying to determine how an intruder managed to overcome your defenses to plant malware on the network. Without accurate and complete data relating to the event, you can be left looking for answers that no longer exist.
It is also a good idea to be aware that some SIEM and network traffic monitoring systems base their pricing on the amount of data you want to store. Keep a watchful eye out for this when you are evaluating solutions. Other appliance-based tools are limited based on the specifications of the system you buy, and an upgrade becomes a replacement appliance which can be expensive. The most flexible option is a network traffic monitoring tool that is software-based and allows you to allocate whatever disk space you think is appropriate.
Mac App To Monitor Network Traffic
4. Associate the data with usernames
Traditional network traffic monitoring tools usually report on activity using IP or MAC addresses. While this is useful information, it can be problematic in DHCP environments if you are trying to find a problematic device. One piece of information that can bring together network activity and devices is usernames. Username association will let you know who is doing what on the network.
5. Check the flows and packet payloads for suspicious content
Many networks have intrusion detection systems at the edge but very few have this type of technology monitoring internal traffic. All it takes is one rogue mobile or IoT device to compromise a network. Another issue I often see are firewalls allowing suspicious traffic through where a rule was misconfigured.
The image below shows an example of this: someone created a rule to allow traffic inbound on TCP 5901 (VLC remote desktop sharing), but they did not limit it to one source and destination. The source addresses in this case appear to be registered in China and connections from this country would not be expected to connect to this network.
Summary
Not all tools for monitoring network traffic are the same. Generally they can be broken down into two types – flow-based tools and deep packet inspection tools. Within these two types you have the choice of tools that use/don´t use software agents, tools that store/don´t store historical data, and tools with intrusion detection systems that monitor network traffic within the network as well as at the network edge.
- Choose flow based analysis tools if you want to get traffic volumes and IP addresses associated with WAN or other layer 3 links
- Choose packet analysis tools if you need traffic volumes, IP addresses and more detail to investigate security or operational issues.
If you would like to discuss any of the points raised in this article, do not hesitate to contact us.
Debugging network activity on an iOS device can be challenging. There are fantastic tools built into Xcode that allow you to to see the data flowing in and out of the device, but troubleshooting network activity at the TCP level can be difficult. Often the best option you have is to perform a packet capture at the router level, but this presents it’s own set of challenges. Capturing packets at the router level casts a wide net and you end up capturing a lot of noise at the router level that can make debugging iOS TCP traffic very time consuming. Also, capturing TCP traffic at the router level does not give you a true perspective of what your cellular traffic looks like as WiFi traffic is often much faster. Luckily, within the last week, I learned that there is a way to expose a remote virtual interface on a iOS device from macOS. Exposing a virtual interface allows you to directly capture TCP traffic that is flowing in and out of the device's network interface. This is a true look at your network traffic from the TCP level, no matter if your traffic is over cellular or WiFi. And that is why I wanted to write this article, to give a brief explanation on how to expose a remote virtual interface on an iOS device and then run a packet capture from that interface. Let's get started!
Exposing a Remote Virtual Interface 📱
A complete writeup on exposing a remote virtual interface is available on Apple's developer documentation, but I wanted to take just the core steps and provide example of them below. To begin, make sure you have the iOS device plugged in and you can see your network interfaces on macOS and the iOS device by typing the following command:
What Is Network Traffic
Next, open up Xcode and navigate to Window -> Devices and Simulators. Here Xcode should have your connected device and your device identifier. Copy down your device identifier because you will need it in the next step.
Next, use the rvictl tool to create and expose a remote virtual interface on your iOS device with your device identifier. To do this run the following command below.
From here you should now be able to see the newly created network interface once you run the ipconfig -l command again. On the terminal again, run that same command as before to see the new interface, rvi0. This is the network interface on the iOS device that you will be able to perform packet capture on!
Running a Packet Capture 🖥
Now for the fun part, capturing the TCP packet trace into a pcap. To do this, queue up your iOS application on your device that will be running your network activity. Next, on the terminal, type this command in to use the TCPDUMP tool to capture the network activity on the remote virtual interface that you just exposed (rvi0):
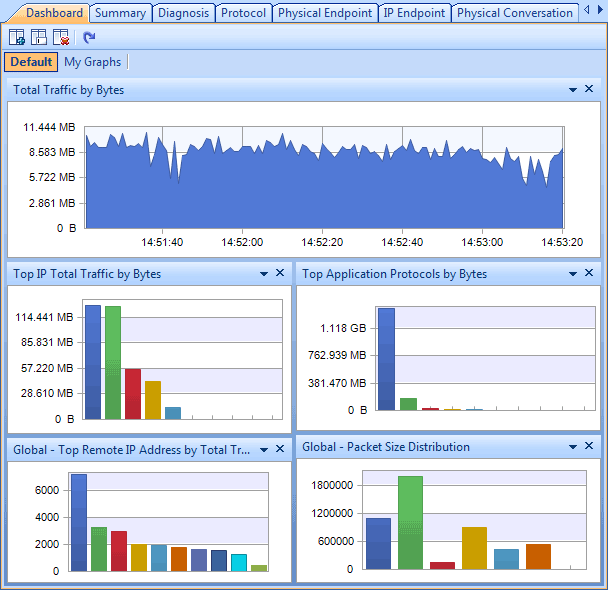
You are all set now to run your network activity on your iOS device and see TCPDUMP capturing your network packets from the terminal. In this example I ran two network requests. The following screen shot below shows a sample of one of my tcp streams in Wireshark.
After you are finished, the last thing I recommend doing is removing your remote virtual interface on your iOS device. To do that, run the command below and you should be all set.
In Summary ⌛️
Mac App Network Traffic Ais
In summary, I hope you have now learned a bit more about how to capture a packet trace directly from an iOS device. I would be interested to hear if this technique also works on tvOS or watchOS? Please write in and let me know if you test this out and you are successful or not.
Mac App Network Traffic Cameras
Network debugging to me is fascinating. One of the most important things is that you need though to be successful is just the data you need about your TCP traffic and this technique can be very helpful for iOS debugging to eliminate network noise at the router level. I hope you have enjoyed this post and please if you have any questions comments or concerns, leave a comment, and I will get back to you as soon as possible. Thank you!